Imagine if you could operate a decentralized Twitter without you or your users having to worry about the server host creating fake tweets or manipulating them. Or perhaps MEV-as-a-service bots that don’t leak your private keys? How about uncensorable decentralized frontends to your favorite dapps without the possibility of the system host injecting any vulnerabilities to the interface?
In this article, we introduce you to enclaves, a privacy-enhancing technology that not only protects the confidentiality of data in it but also ensures the integrity of the operations performed on it, provided you trust the enclave manufacturer ;)
Introduction to Secure Enclave
Consider a black box with a private key to which you can supply encrypted data. The data can thus only be decrypted inside the black box. Outside the black box, it’s just a garbled bunch of characters. The black box can thus be supplied with the most private info with the assurance that no one outside it will be able to make any sense of the inputs. If this black box is a special hardware chip separate from the computer’s usual processor with the private key literally hardcoded in it, even the operating system or any other normal system process can’t access it. Call such a black box, enclave.
Since an enclave is isolated at a hardware level, there’s little any software program can do to decrypt or manipulate contents in it. As the data in question can be programs themselves, enclaves can also ensure that any algorithms supplied to them will be computed on the data supplied to them as coded. This ensures the integrity of operations performed inside an enclave.
To understand it better, let's start with the basics on states of data and get clarity on the context in which we will be discussing Secure Enclaves.
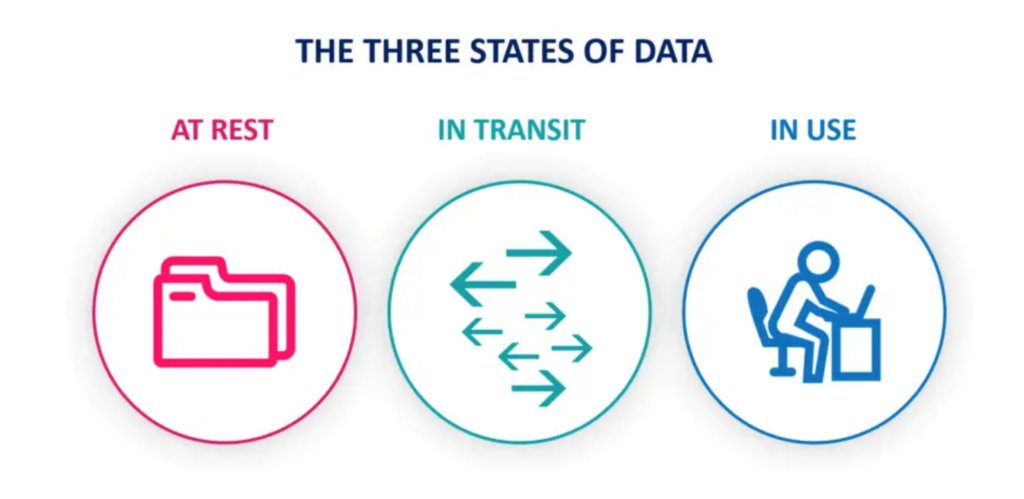
States of Data
Data can exist in any one of the following three states:
- Data At-Rest: Data is stored on some device like a hard drive or on the cloud.
- Data In-Transit: Data being moved from one point to another.
- Data In-Use: Data being operated upon or on which computation is being performed.
To secure data at each of these states, some encryption/security mechanisms may be applied which are respectively as follows:
- Encryption At-Rest: Data stored is in encrypted form and/or with password protection. E.g. encrypted cloud storage, password protected USB drives.
- Encryption In-Transit: Data to be transferred is first encrypted and then sent. E.g. Transport Layer Security (TLS).
- Encryption In-Use: Data privacy is provided while it is in use by isolating data and computation.
The problem
In traditional systems, sensitive data may be secured At-store or In-transit, but it needs to be in non-cypher/decrypted form while in-use. Sensitive data could be in memory or some register during computation and any malicious entity with access to it can learn about sensitive data or can perform various side channel and timing attacks to get some insights into the data.
This is an important and challenging problem as these days most of the computation is done remotely on the cloud where trust depends on the cloud provider and the application deals with lots of sensitive data like PIIs, financial data, etc., which has very strict regulatory policies like GDPR, CCPI, HIPAA, etc.
The solution
Pure Cryptographic Approach:
Cryptography like Secure Multi-Party Computation (MPC) and Homomorphic Encryption (HE) can be used to perform private computation on sensitive data. It comes with the advantage that it works on regular computing hardware but has limitations of not being efficient enough as they have more latency, are computationally expensive, and are not general purpose.
Secure Enclaves Approach:
The Secure Enclave approach is based on the idea of enclaving data where the data and the computation performed on it is isolated from the regular application computing unit. Enclaves primarily have 3 implementations which are as follows but the core idea is isolation.
Secure enclave implementations
- Special hardware component
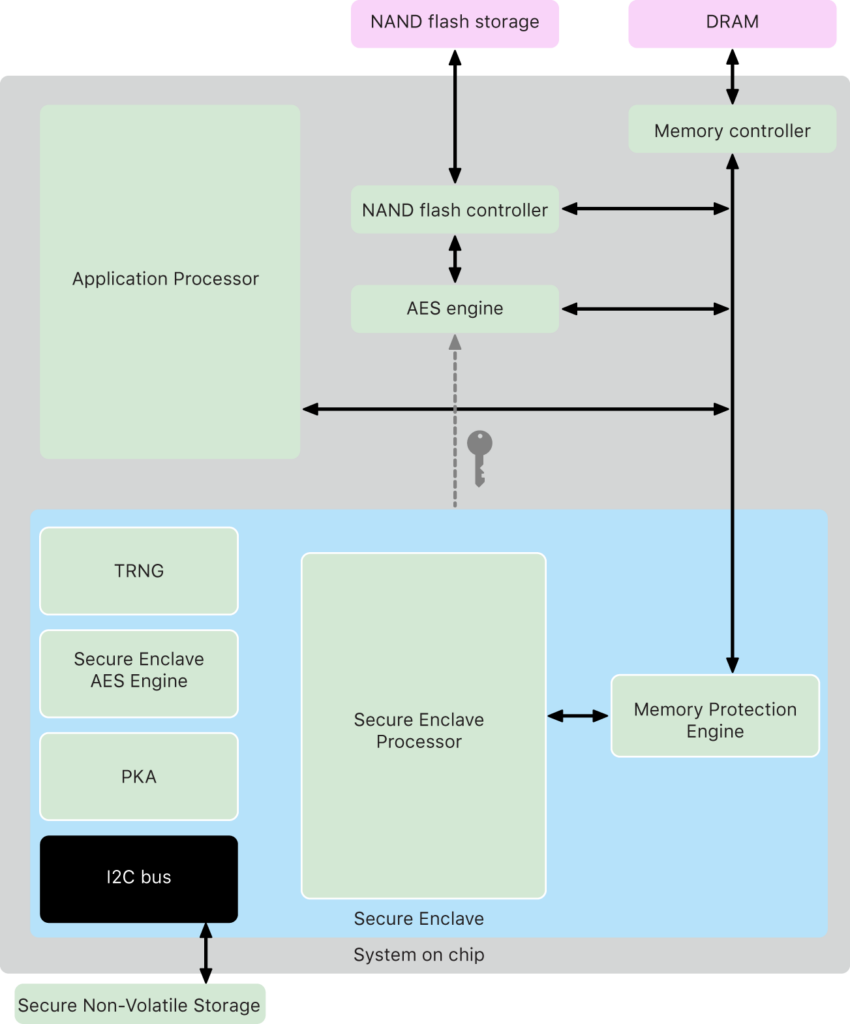
In this implementation approach, a special computing unit i.e. a coprocessor is introduced to create a physical separation from the CPU. Apple’s Secure Enclave implementation is based on this approach and was introduced in the iPhone 5s. It is used for securely storing sensitive data like PIIs for touchID, faceID, etc, and secret keys for keychain, Apple Pay, etc. Along with secure storage, the coprocessor has a few algorithms implemented for operating on that data e.g. signature generation and verification.
The advantage of this approach is that it provides pretty good isolation but has a limitation of specialized computation and limited support e.g. support for only a few elliptic curves. Another example similar to this can be the ledger hardware but as an external connected component instead of an on onboard coprocessor.
- Upgrading existing hardware
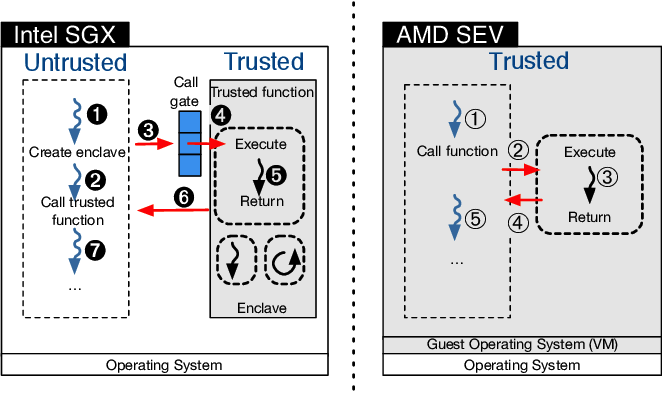
In this implementation, existing hardware is upgraded to support enclaving by introducing a new instruction set. Intel SGX (Software Guard Extensions) and AMD SEV (Secure Encrypted Virtualization) are based on this implementation. In terms of computation and storage it does not have any limitation but the tradeoff is that it uses main memory for storage and secures data by encrypting it and providing no access to even privileged software like kernel.
- VM based enclave
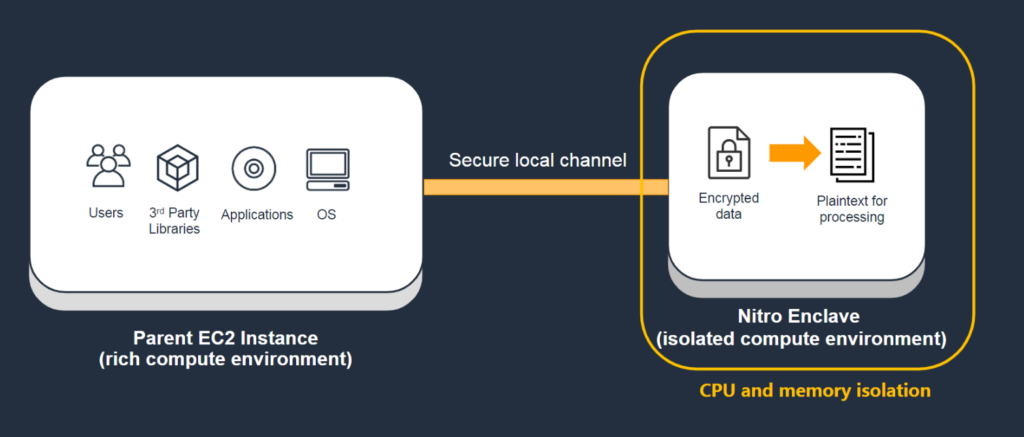
In this approach, enclave implementation is software/VM based, unlike the previous two that were hardware based. The Amazon nitro enclave is the implementation based on this approach; it has a special enclave VM that runs in nitro hypervisor. Nitro Enclave is a hardened and highly constrained VM with no persistent storage, no interactive access and no external networking.
Conclusion
Enclaves are a powerful primitive that have a variety of applications in blockchain, healthcare and medical research, finance, mobility, etc. Due to an embedded trust assumption on the honesty and correctness of the hardware manufacturer, they probably aren’t secure enough to be the backbone of a global decentralized currency. However, the tradeoff is probably worthwhile for several other commercial and non-profit applications. Secure enclaves service on top of a layer 0 relay network can provide a robust infrastructure for building uncensorable applications. I look forward to posts and designs from researchers working in the area to enhance the Marlin network with such capabilities.
Follow our official social media channels to get the latest updates as and when they come out!
Twitter | Telegram Announcements | Telegram Chat | Discord | Website